Imagine your digital life as a house full of valuables – photos, messages, bank details and more. Cybersecurity is like putting locks, alarms, and guards on that house to keep thieves out hacksheets.in cisco.com. In simple terms, cybersecurity means using tools and practices to protect computers, phones, networks, and data from digital attacks. Cisco defines it as “protecting systems, networks, and programs from digital attacks,” while IBM adds that it protects “people, systems and data from cyberattacks” using technology, processes and policies cisco.com ibm.com.
What does this look like in everyday life? Think of having strong passwords and encryption as sturdy locks on your digital doors, and antivirus software as a security guard watching for break ins hacksheets.in hacksheets.in. Just as you wouldn’t leave your front door unlocked, you shouldn’t leave your computer or phone without basic protections hacksheets.in hacksheets.in. In short, cybersecurity is about keeping unauthorized users (hackers) away from your digital information hacksheets.in cisco.com.
Why Cybersecurity Matters
Cyber attacks can have serious consequences. Cisco warns that for businesses, a hack can mean “financial loss, operational disruption, data breaches, and loss of trust,” while for individuals it can mean “identity theft, financial fraud, and privacy invasion” cisco.com. In 2025, cybercrime is projected to cost the world economy over $10.5 trillion per year ibm.com more than many countries’ entire GDP.
- Personal Impact: A hacked email or social account can leak photos, reset your accounts, or steal money.
- Business Impact: Companies hit by ransomware or data breaches can be forced to shut down, lose customers, and face huge fines. (IBM’s research shows the average data breach now costs about $4.88 million ibm.com.)
- Global Impact: Governments and critical services (like hospitals and schools) rely on secure systems. Attacks can disrupt power grids or emergency services, affecting whole communities. In fact, the education sector alone saw the highest number of weekly attacks per organization in early 2023 techloy.com highlighting how anyone can be targeted.
Attacks vary by sector. For example, in Q1 2023 the education sector averaged 2,507 attacks per organization per week (a 15% rise), and retail/wholesale saw the fastest growth in attacks (49% jump) techloy.com. Such trends show that even schools and small businesses are in hackers’ crosshairs.
The bottom line: everyone and every device connected to the Internet is a potential target. As Cisco puts it, in today’s connected world “everyone benefits from advanced cybersecurity solutions” cisco.com. Protecting yourself and your data isn’t optional – it’s essential.
Common Cybersecurity Threats
Cybersecurity fights many types of attacks. IBM and Microsoft both highlight the main threat categories ibm.comibm.com. Here are some common cyber threats:
| Threat | What It Is | Example |
|---|---|---|
| Malware | Malicious software (viruses, worms, trojans) designed to harm devices or steal data ibm.com. | A USB “Trojan” program that secretly copies your files. |
| Phishing | Fraudulent emails or messages that trick you into revealing passwords or downloading malware ibm.com. | A fake bank email asking you to “reset” your password. |
| Ransomware | A type of malware that encrypts your data and demands payment to unlock it ibm.com. | The WannaCry attack that encrypted files on thousands of PCs. |
| DDoS Attack | Overloading a website or service with traffic to take it offline, using hijacked computers (botnets) ibm.com. | Flooding a gaming server so it can’t connect players. |
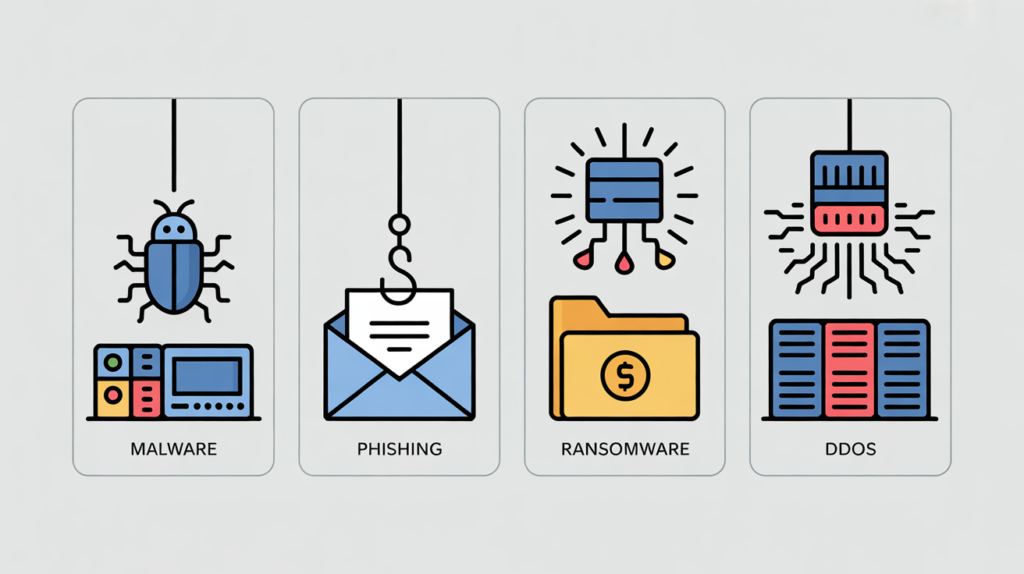
These are just examples. Hackers are always inventing new tricks. For instance, AI tools like Chatgpt are now used to craft more convincing phishing emails techloy.com, and stolen passwords (identity attacks) still make up roughly 30% of all intrusions ibm.com. The key is to recognize the basic threats so you can guard against them.
Layers of Cybersecurity: People, Process & Technology
Effective cybersecurity is multi-layered. IBM and Cisco both stress that it’s not just about one tool or one check. Cisco explains that people, processes, and technology all work together to defend against attacks cisco.com. For example, you might have a strong firewall and antivirus (technology), but without trained users (people) who avoid suspicious links, an attack can still succeed.
Some common defenses include:
- Firewalls and Network Protections: Like walls around a castle, a firewall blocks unauthorized access. Cisco notes typical defenses like next-generation firewalls, DNS filtering, and antivirus software for networks and devices cisco.com.
- Strong Passwords & Multi-Factor Authentication (MFA): Passwords are like keys to your house hacksheets.in. Using unique, strong passwords and adding a second factor (like a code from your phone) acts like a double lock for your account hacksheets.in.
- Software Updates: Software often has “patches” to fix vulnerabilities. Keeping your apps and operating system up-to-date is like repairing broken windows or doors hacksheets.in. Outdated software is one of the easiest ways attackers get in.
- User Awareness and Training: People are often the weakest link. Training students and employees to spot phishing and to follow security practices (e.g. not sharing passwords) is crucial. A culture of security-awareness is a powerful layer.
- Backups: Regularly save copies of your important data (photos, documents) in a secure place. That way, if you do get hit by ransomware or a hard drive fails, you can restore your files – similar to having home insurance hacksheets.in.
Modern cybersecurity uses advanced technology to keep data safe. As Cisco highlights, tools like encryption, secure cloud services, and endpoint protection all play a role cisco.com. For instance, using a VPN or encrypted connection is like sending your data through a hidden tunnel where eavesdroppers can’t see hacksheets.in.
In a nutshell, no single solution will protect you. You need a combination: good habits by people, sound security policies and processes, and up-to-date technology. When all these layers work together, your digital “house” is much harder to break into.
Cybersecurity for Students and Businesses
Who needs cybersecurity? Everyone. For students and individuals, it means protecting personal info on phones, laptops, and social media. For small businesses and organizations, it’s about safeguarding customer data, financial information, and uptime. Cybersecurity Ventures reports that small businesses are now common targets – after a serious breach, over 60% of them are forced to shut down within six months deepstrike.io.
- Students: Even teens are targeted by social media scams or fake tech support. Using shared or school Wi-Fi requires care (don’t click unknown links on school email!), and always lock your devices.
- Entrepreneurs and Business Owners: If you run a shop or startup, a cyberattack could halt sales or expose customer records. Industry surveys find that budgets often lag behind threats, so awareness and basic defenses (firewalls, employee training) are key. As Cisco points out, critical sectors like hospitals and utilities must be secured because society depends on them cisco.com.
- Remote Workers: With more people working from home, home routers and personal devices must be secured. Unsecured devices create new “attack surfaces” for hackers to enter your company’s network ibm.com.
In short, treating cybersecurity like insurance and maintenance is smart for everyone. IBM recommends embracing recognized frameworks (like the NIST cybersecurity framework) to guide these efforts, and continuously monitoring systems for intrusions cisco.com ibm.com.
Conclusion
Cybersecurity might seem complex, but at its core it’s simply protecting your digital life. By understanding the threats (malware, phishing, ransomware, etc.) and adopting basic defenses (strong passwords, updates, antivirus), you can stay a step ahead of hackers. Remember: security is an ongoing process, not a one-time fix.
Stay informed and stay cautious. Share this guide with friends or colleagues so they can also keep their data safe. If you enjoyed this article, leave a comment with your own tips or questions, and consider subscribing for more simple tech explainers. Together, we can make the internet a safer place for everyone.

